Socially Engineered Fraud: More of A Threat Than Most Business Owners Realise
Despite how prevalent socially engineered fraud is becoming, lots of small businesses forgo basic IT security strategies that could protect them against these threats. We see these problems quite often across all sectors of businesses, but due to the larger sums involved and the kind of data held, architectural, construction, and property management services are now being targeted.
Take for example a situation we encountered recently with a new client of Mac Support London. This particular company had high net-worth & ultra-high net worth clients. In order to manage these clients, they were storing their AML and KYC data on a popular cloud storage system that distributes the content to every device. To compound this issue, they had zero endpoint security in place & no defined IT strategies, such as password complexity policies, two-factor authentication. As a result, they were in serious breach of various laws not to mention putting themselves and their hard-earned company reputation at serious risk.
AML/KYC data are essentially the golden keys for criminals looking to exploit identity-related fraud. That’s because Anti-Money Laundering (AML) and Know Your Customer (KYC) is the process of verifying the identity of clients. This requires getting information such as names, dates of birth, addresses, copies of ID documents.
Now let’s get into what social engineered fraud is and how to protect yourself.
What is Social Engineered Fraud?
Social Engineering is a method of fraud where criminals exploit human
These are not traditional hackers looking for software vulnerabilities. Although they do exploit software to get at the information they seek.
How At Risk Are You?
Small to medium-sized business owners often assume hackers/cyberattacks only target large businesses. That’s simply not the case. Any business who’s relationships deal with larger than average transactions such as property management, construction firms and architects are just as vulnerable. After all, you too must collect AML/KYC data from your clients. And this type of data is a target for phishing scams.
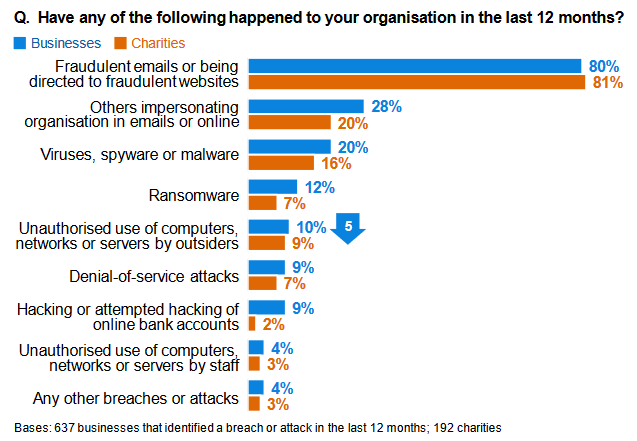
Phishing is one of the most popular types of socially engineered fraud. It is the highest cyber threat faced by over 80% of UK businesses that dealt with a cybersecurity issues across 2018-2019.
We are now seeing ever more creative attempts to access people’s data. In once such incident the fraudster sends an email that seems to be coming from a trusted source. Often, this email, can appear during an email exchange and offers a file to view or a link to follow. Often the link will take you somewhere that looks exactly like your normal cloud-based file services or webmail interface and asks you to enter your credentials in order to view the file. Once handed over you may even be able to view a benign file with no malicious payload. The aim was to get access to your data to see what is there. Once “Inside” The hacker will try to understand the internal relationships and external client relationships and then further penetrate your systems and send more, trusted source phishing attempts.
So, all businesses are vulnerable unless they put in place the right measures to protect themselves and their clients.
How to protect against socially engineered attacks
From a technical standpoint, there are a few things that need to be happening
First, build a security strategy that includes
- a secure password policy
- DMARC domain spoofing policies
- two-factor authentication
- configure mobile devices with remote lock & wipe
- employ an endpoint security solution that is centralized and managed across your entire device ecosystem
- create country-specific access definitions for cloud-based email services
- configure alerts and monitoring services where possible. (365, G-Suite)
Monitor, Monitor & Monitor!
Implement an Information Security Culture
Employee actions are what drives socially engineered attacks. Because of this, it’s important that your staff understands how to identify these acts, how to prevent them, and what to do if it happens. This should include:
- evaluating your security culture and policies;
- creating a strategic plan that includes an awareness program;
- implementing the identified changes.
Improve Awareness
Increase the awareness level of yourself and your staff to prevent being victims of these attacks. Things you can do and teach your team include:
- To think before you click. Phishing attacks often employ a sense of urgency, so think before you respond or click.
- Not downloading files that you don’t know or the sender
- Being careful of unsolicited messages, especially those asking for information
You can also invite a security expert to deliver an in-depth training to your staff on the issues.
Upgrade your Technical Capacity
By taking simple steps to harden IT security and strategising against these threats, you can mitigate massive reputational losses where social breaches occur.
So, combating these attacks, particularly where small businesses are concerned, requires rethinking set and forget cloud email services. You need to ensure that your 365, G-Suite systems are monitored. Or, at the very least, how you use them adheres to best practices and facilitates adapting to these new threats.
Next, update your endpoint security strategies. Ensure you protect your business and client data before they make an attempt. Where an in-house security expert is not feasible, a full-service managed IT team can help you protect your business data.
